You have ever wondered how a group of hackers crashes a website. It’s pretty standard nowadays hearing about news like some X.Y.Z. website was taken down by some hackers or something like that. But have curiosity ever hit you about how all this takes place.
Actually, there are several methods to do that. Among which, the DDoS or the Distributed Denial of Service Attack is most common. Here in this article, we are going to discuss this method.
Table of Contents
What Is DDoS? What is Its meaning and Full Form?
DDoS stands for Distributed Denial of Services. It belongs to the more straightforward denial-of-service attacks’ family as the biggest brother among all of them.
This is the most commonly used attack which is purposely used for crashing or taking down a particular website.
A DoS (Denial-of-services) attack generally consists of one source that sends information. But in the DDoS attack, this source section can have a massive amount of sources. This “very huge” amount generally consists of thousand of or hundreds of thousands of P.C.s or other internet-connected devices. And this makes this attack much more effective than its siblings.
How DDoS works?
A DDoS attack generally works on the principle of flooding the webserver/host infrastructure with a vast amount of data. This data exists in such a large amount that it exceeds the limit of the processing power of the website hosting.
Usually, every web server has its capacity for processing the requested operation, just like every other computer. And DDoS attack takes advantage of this by flooding the server with a very very large amount of requests at one time that it can’t handle. This results in the server experiencing a sudden lag or a temporary shut down and ultimately resulting in a website crash or a temporary downtime.
Is DDoSing illegal?
Short and simple. Yes. Performing a DDoS attack is completely illegal if done without the permission of the victim. Under the Computer Fraud and Abuse Act, performing a DDoS attack on a network without permission can lead the attacker up to 10 years of imprisonment or a fine of up to $500,000 or even both in some cases.
Hence yes, DDoSing is illegal.
How To DDoS Someone?
Well, there are several methods to do so. The DDoS attack requires a massive/unlimited internet bandwidth so that you don’t get out of data while performing the attack. Here I am gonna discuss some of the common methods of performing DDoS like DDoS using command prompt (cmd), using Google Spreadsheet, and with some automatic tools like L.O.I.C.
Warning: All the shared information and procedures are purely and solely for educational and learning purposes. Tme.net never supports illegal works and also never asks its readers to perform any DDoS to take down websites.
Performing DDoS with C.M.D. (Manual Method)
The DDoS performed via cmd is generally one of the most basic DoS attacks and is usually known as “Ping of Death“. It uses Command Prompt to extensively flood the I.P. address with data packets.
This attack works best against small targets like a single P.C. or a wireless router, etc.
Performing a DDoS attack on a simple website by using command prompt includes the following simple steps:
- Select a small website, or you can use your own to perform the DDoS attack legally for the learning purpose.
- Now find the I.P. address of the website that you have selected for the attack. To find the I.P. address of the website type the following command in cmd and don’t forget to replace <website URL> with the URL of the website:
ping <website URL> -t
- Now when you are ready with the I.P. address run the following command:
ping [IP Address] -t -1 65500
- Now, since its a manual method, you will have to run this command continuously for 2-3 hours. You can use more P.C.s/devices at the same time to target the website.
- If you perform the attack correctly then you will find that the website is showing “website is temporary down” or “server unavailable” message.
Performing DDoS using Google Spreadsheet (Manual Method)
The Google Spreadsheet seems to be a utility tool for managing and organizing your data. But do you know that using Google Spreadsheet is also a very effective way to perform a DDoS attack? Yes, you heard it right.
An attacker can use Google Spreadsheet to continuously ask a website to provide a particular file stored in the cache. In most cases, the file is an image or a pdf which generally stored in the website server with a good amount of file size. Continuously asking the website for that particular image/pdf can easily result in the website performing slowly, which will eventually result in a temporary sleep.
One such example is the use of Google’s feed fetcher crawler. Google uses this crawler to fetch the image and display its cached version. Google uses the same technique to display images stored in the =image(“”) value.
An attacker can utilize this as a weapon to send a random parameter request asking the feedfetcher to crawl the same file of the same website again and again. Resulting the website get flooded with a tremendous amount of requests. You can read this case that took place when a blogger accidentally attacked himself, which resulted in a huge traffic bill.
And if he/she uses a pdf file’s URL, then Google wouldn’t display anything but will continuously crawl that particular URL. In such a case, there will be no bandwidth loss from the attacker’s internet connection as crawling is being done b/w Google and the targeted website with no fetching on Google Spreadsheet whatsoever.
And in such a case the spreadsheet function will be something like this:
=image(“http://example.com/sample.pdf?r=0”) =image(“http://example.com/sample.pdf?r=1”) =image(“http://example.com/sample.pdf?r=2”) …… …… =image(“http://example.com/sample.pdf?r=999”) =image(“http://example.com/sample.pdf?r=1000”)
DDoS using tools like L.O.I.C. (Automatic Method)
If you find both of the above mentioned DDoS methods to be safe just because they are manual. Then you should be worried as there are so many DDoS tools out there that make the whole process automatic. On such tool is L.O.I.C. or Low Orbit Ion Cannon.
Here is how a small scale hacker/attacker can use the L.O.I.C. tool for DDoS.
- After managing the L.O.I.C. tool from somewhere and installing it, he sees the following L.O.I.C. interface.
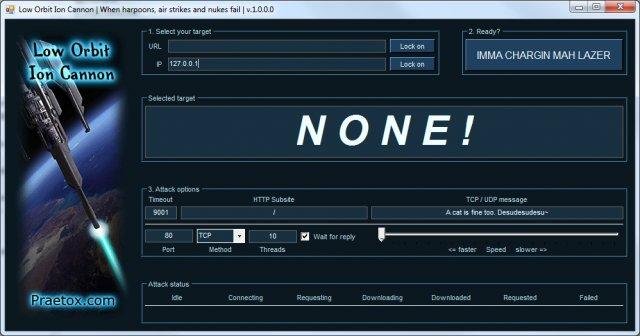
- After filling the fields like URL and I.P. (optional) he would lock on the target.
- The attacker usually keeps the timeout, HTTP subsite, and speed bar options as it is along with port value set to 80, method set to U.D.P., and thread value to 10 or 20.
- Unchecking the Wait for reply option favors the hacker, and then he just hits the “IIMA CHARGIN MAH LAZER” button.
That’s it. After running the DDoS tool for about half an hour, the targeted website should be down.
DDoS Tools: Used By Hackers
The most commonly used DDoS attacking tools by hackers are as follows:
- L.O.I.C. or Low Orbit ION Cannon
- H.O.I.C. or High Orbit ION Cannon
- Refref
- Slowloris
- R U Dead Yet? (R.U.D.Y.)
- HULK or HTTP Unbearable Load King
Final Verdict
Basically, DDoS is a network vulnerability that is almost impossible to avoid. Moreover, it is very hard to detect the attacker. Because this attack is performed by using so many devices to send traffic on a specific URL or I.P. to make it down. The traffic can be from a different location to make it even hard to detect the attacker. There is always a possibility remains that the attacher is using hacked devices to send that traffic.
At the current scenario, there are some services like Cloudflare that help to reduce the DDoS attacks working as a middle man. You might be aware, Cloudflare works as a proxy between the origin server and the surfing users. So, it is able to prevent these attacks at some levels by re-routing traffic on its own servers. Overall, there is still a requirement to find a working solution to stop these kinds of attacks!